For this question, check all that apply.
Consider executing each of the following code sequences on the
pipelined MIPS implementation given below:
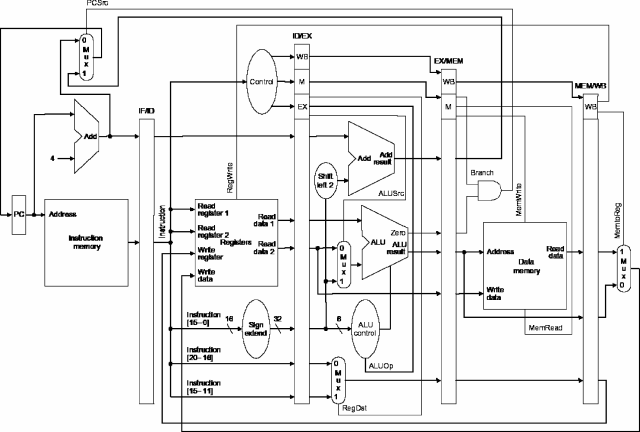
Which of the following statements best describes
the execution times you would expect to observe?
(A) addi $t1,$t0,4
lw $t2,0($t1)
xor $t2,$t2,$t3
(B) addi $t1,$t0,4
lw $t2,0($t0)
xor $t4,$t0,$t3
(A) would be sped up if we used value forwarding
(B) would be sped up if we used value forwarding
(A) would be faster than (B) without value forwarding
(B) would be faster than (A) without value forwarding